Featured images gallery
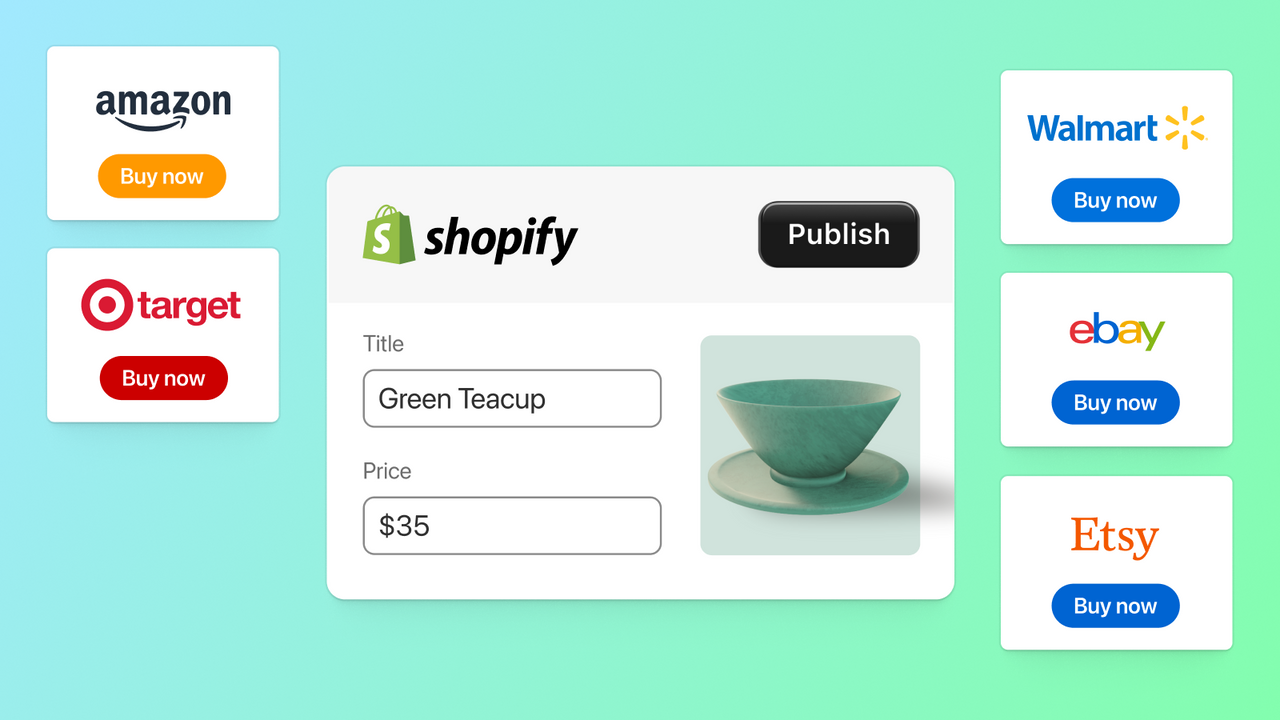
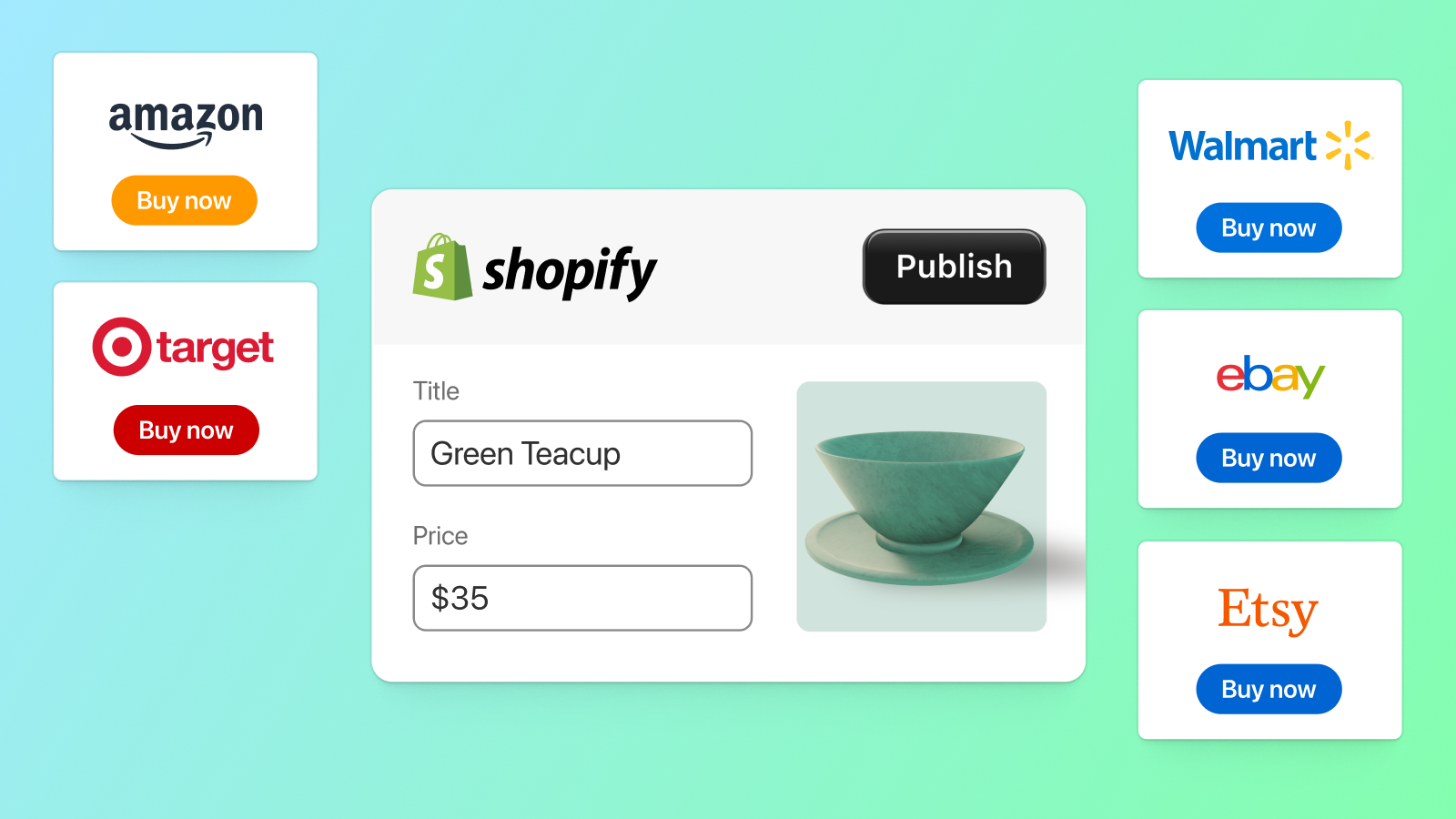
Sell across marketplaces like Amazon, Target Plus, eBay, Walmart, & Etsy. Manage it all in Shopify
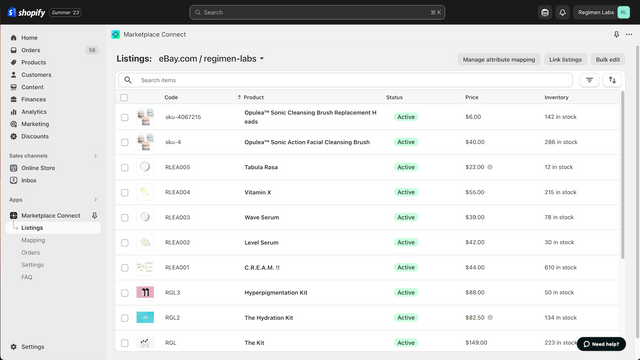
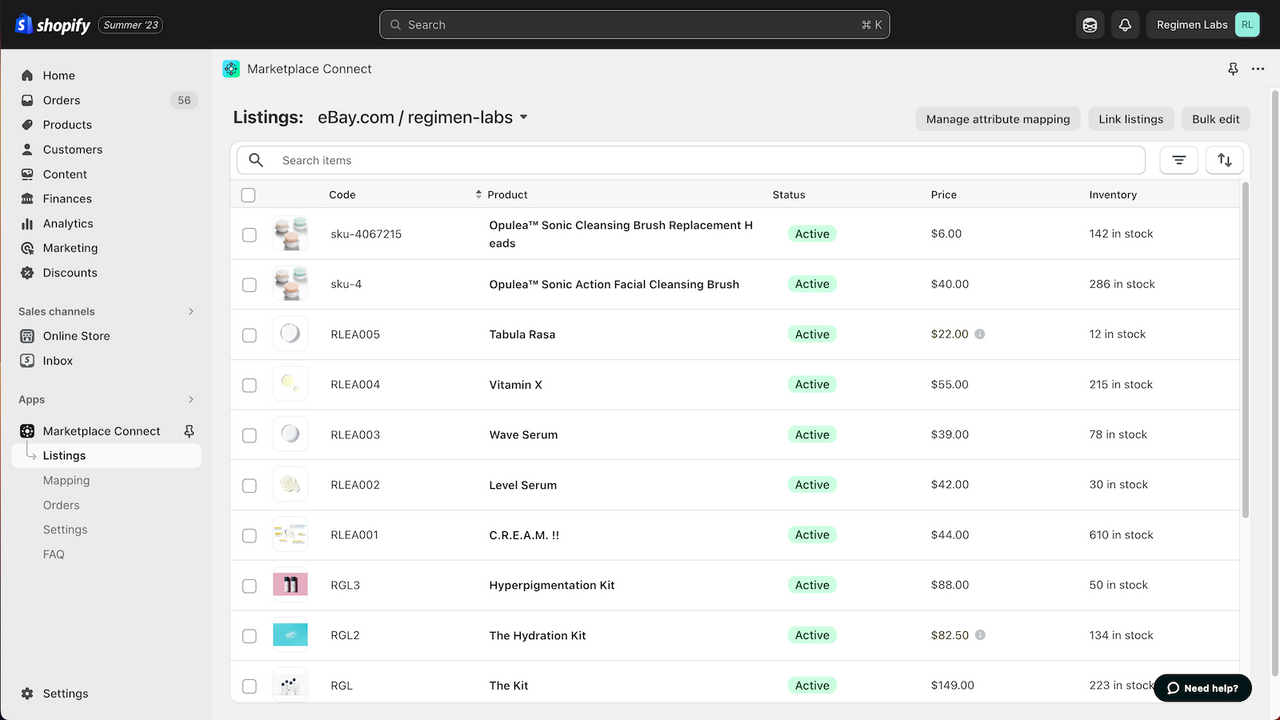
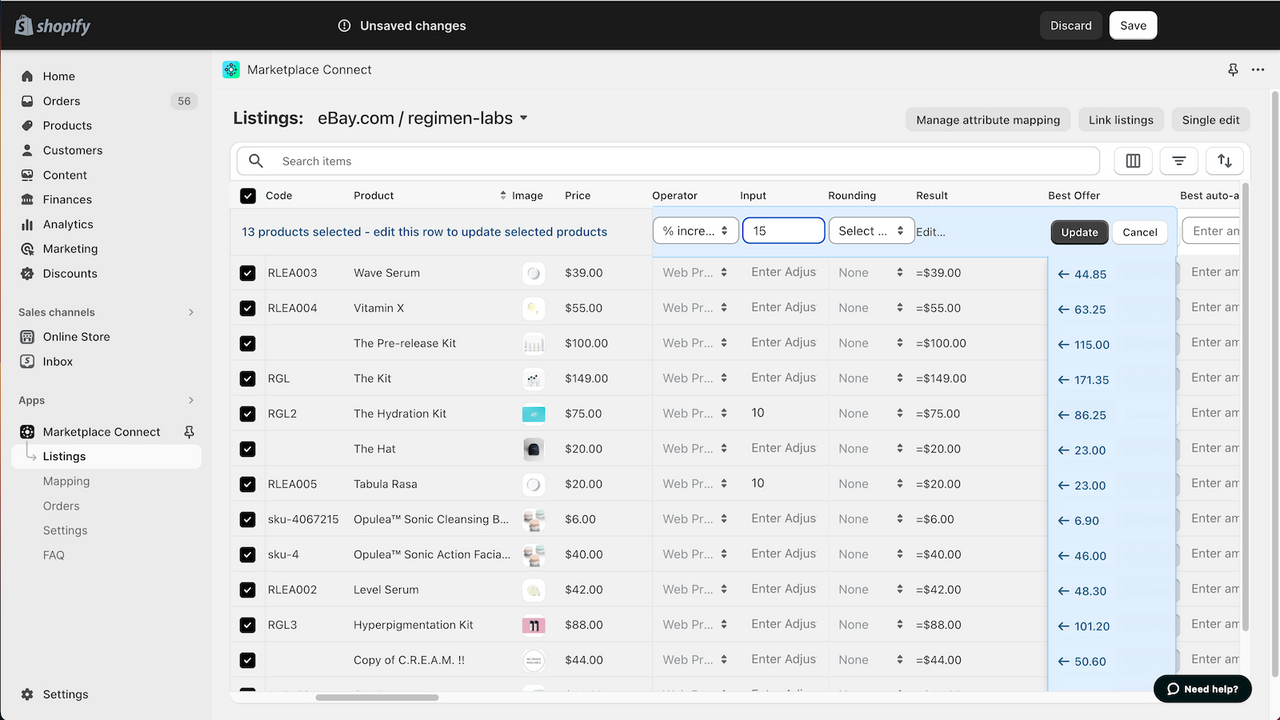
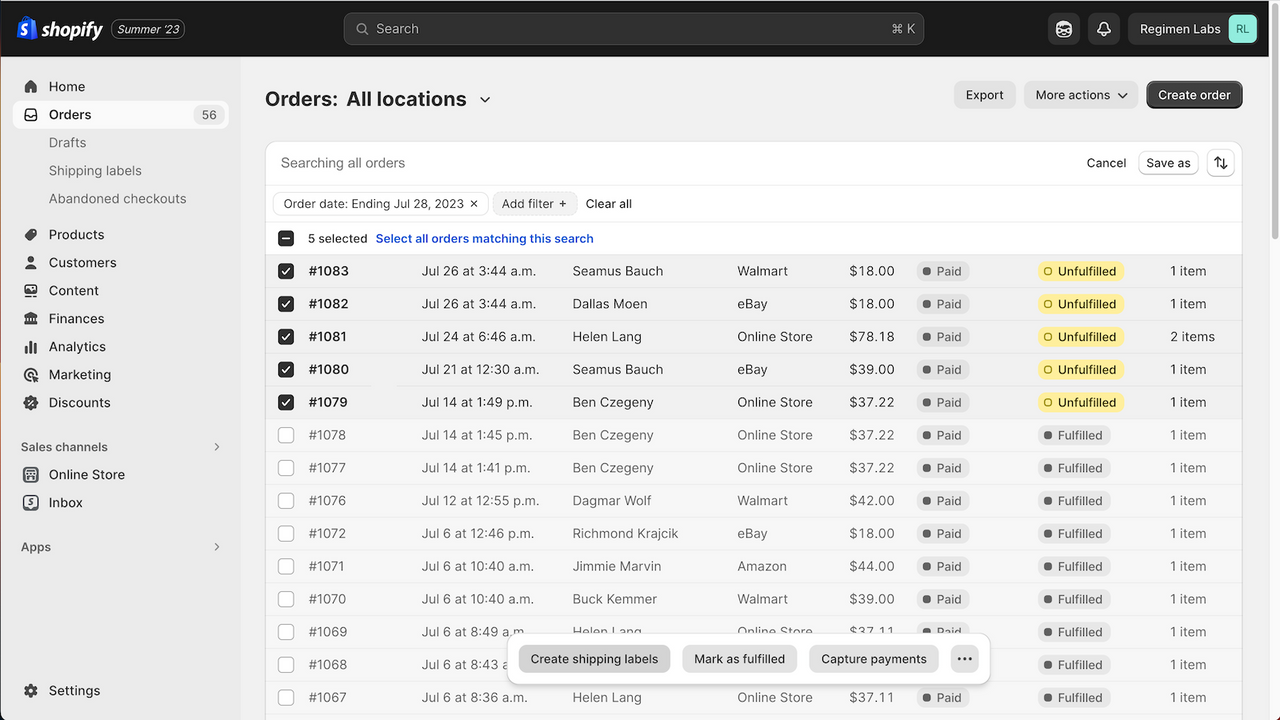
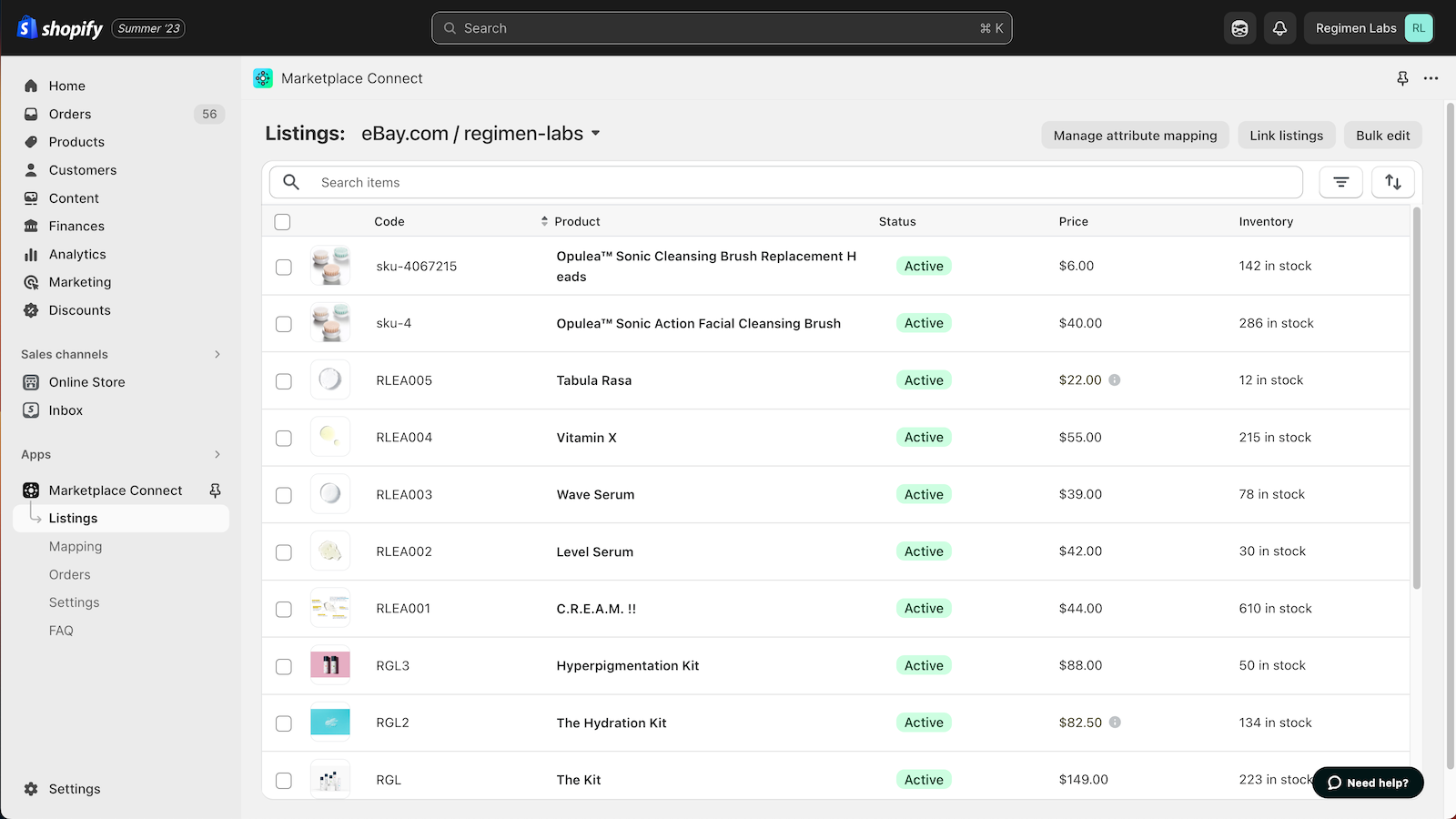
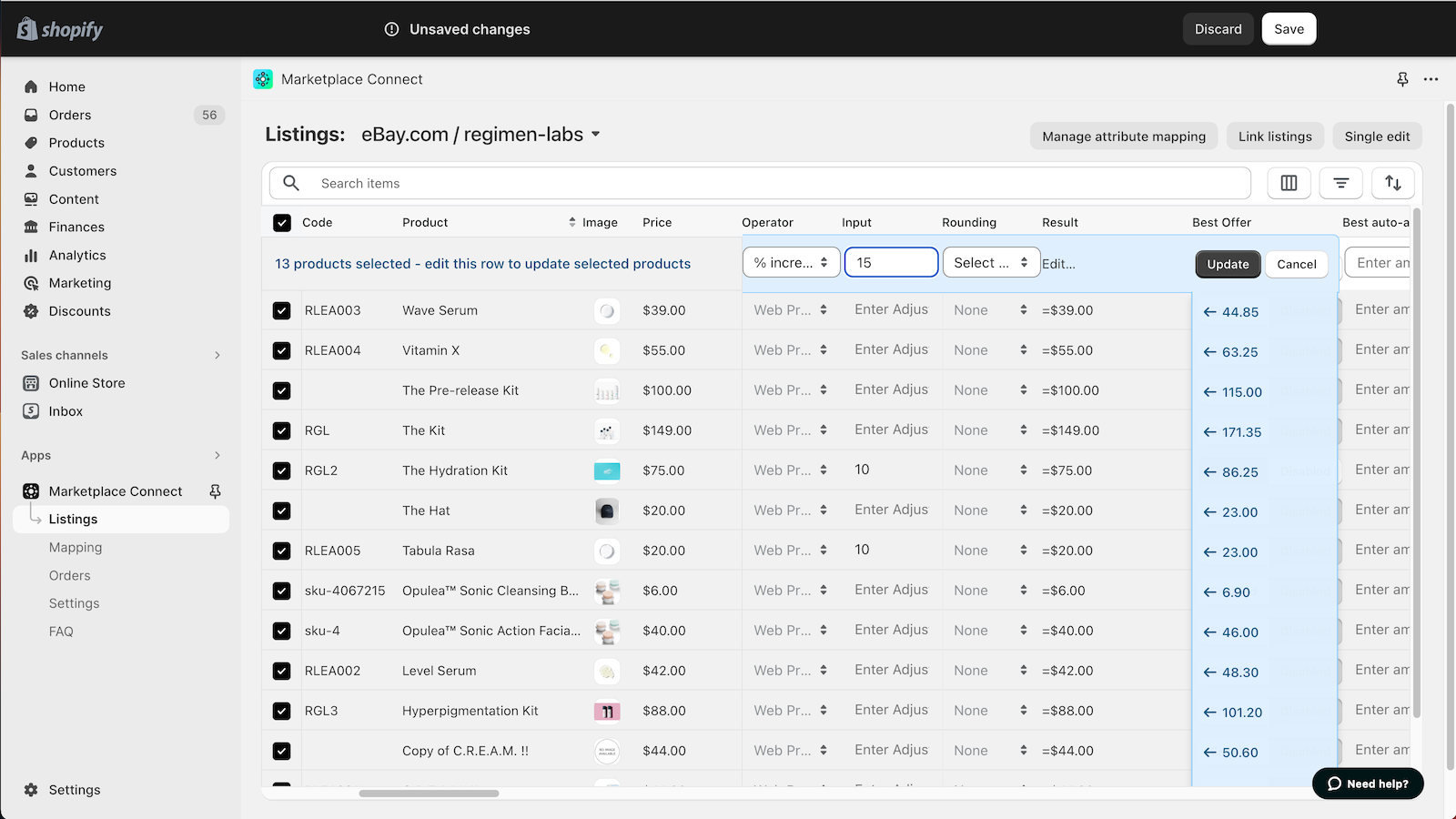
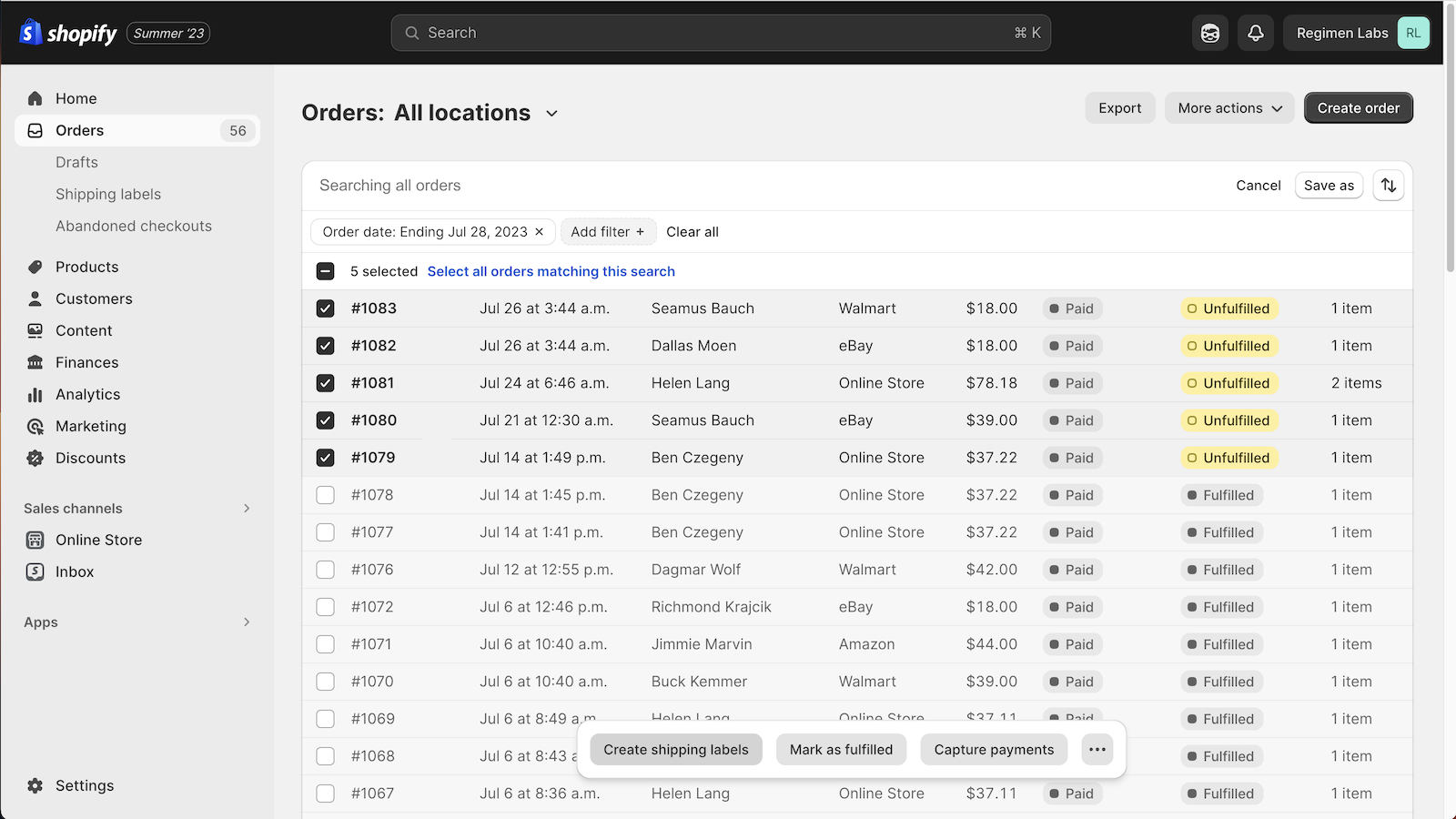
Shopify Marketplace Connect (formerly Codisto) is the fastest and easiest way to sell across top global marketplaces like Amazon, Target Plus, Walmart, eBay, and Etsy. A single app to connect and integrate your Shopify product catalog with multiple marketplaces to effortlessly manage and synchronize listings, orders, inventory, and measure performance all from one place, Shopify.
- Sell products on marketplaces like Amazon, Target Plus, eBay, Walmart, and Etsy
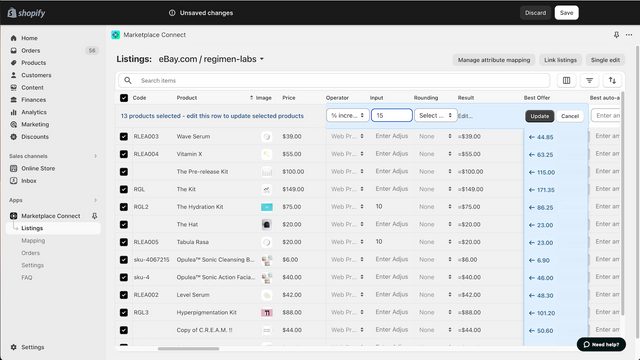
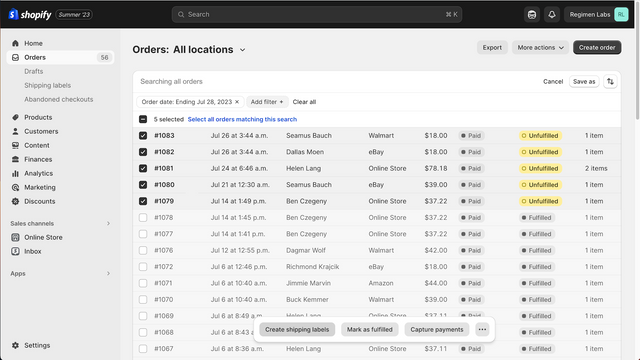
- Manage listings, orders, & inventory in Shopify with real-time marketplace sync
- Flexible fulfillment options to support integrated channel strategies
- Unlimited marketplace account connections for supported marketplaces
- Sell in all marketplace regions and categories with built-in currency conversion
- Highlights
- Popular with businesses in United States
- Use directly in Shopify admin
Languages
English, German, Spanish, French, and Italian
Works with
- Amazon
- Target Plus
- Walmart
- eBay
- Etsy
Categories
Listing management
Data migration
Pricing
Free
Free to install
First 50 marketplace-synced orders/mo free, 1% fee per additional synced-order, capped at $99/month
All charges are billed in USD. See all pricing options
Reviews (2,144)
What merchants think
This is generated by Shopify Magic. It's shown when an app has 100+ reviews and a 4.0 overall rating.
This is generated by Shopify Magic. It's shown when an app has 100+ reviews and a 4.0 overall rating.
Feedback submitted
Merchants highly value this app for managing inventory and orders across multiple channels like Etsy, eBay, and Amazon, using Shopify for synchronization. It's particularly useful for resellers, ensuring consistent inventory and pricing. The interface is user-friendly and continuously improving. Support is frequently praised for being quick and effective, especially the live chat service. Merchants appreciate the app's comprehensive functionality and responsive customer support.
First off the customer service is top notch. While I was learning how to use this app they have been nothing but helpful and patient with answering my questions. I also mistakenly caused an issue with my ebay template. Chloe took the time along with Ediline to figure it out and correct my issue. A+ all the way support. I also tried a few other inventory management apps and chose Marketplace Connect as being better than the rest for my store. It's been the solution i needed all along and look forward to the growth of my store because of it. Thank you!
I had the absolute pleasure of working with Rep Joy from Shopify Marketplace Connect, and I cannot say enough about how incredible she is! Joy is not only extremely knowledgeable and talented, but she is also such a delight to work with.
My account had been stuck for months due to countless listing errors that I just couldn’t seem to resolve. I even hired a freelancer over a month ago who claimed to be an expert in product listings and error corrections, but unfortunately, the problems persisted.
After feeling completely frustrated, I finally reached out to Shopify Marketplace Connect, and that’s when Joy stepped in and worked her magic! In no time at all, she identified and corrected every single issue with ease. It was truly impressive to see how quickly and professionally she handled everything.
Thanks to Joy, my account is now fully functional, and my products are listed correctly. I’m beyond grateful for her expertise and efficiency. If you ever need support, I highly recommend asking for Joy—she’s an absolute superstar!
Exceptional support! I faced an issue with products not showing in the collection, but the team resolved it incredibly quickly. Within just 15 minutes, the app was working perfectly again. Thank you for the swift and efficient service!
Support
App support provided by Shopify.
Get supportFeatured in
More apps like this